In today’s digital age, where data serves as the lifeblood of organizations, protecting sensitive information is paramount. As regulatory requirements grow more stringent and cyber threats become increasingly sophisticated, organizations must adopt robust measures to safeguard their data assets and ensure compliance with industry standards. At the forefront of data protection efforts lies Data Loss Prevention (DLP), a multifaceted approach aimed at identifying, monitoring, and controlling the flow of sensitive data within an organization. In this comprehensive guide, we delve into the intricacies of DLP, exploring its key components, challenges, best practices for implementation, and the various types of DLP solutions available.
Understanding DLP: A Compliance Imperative
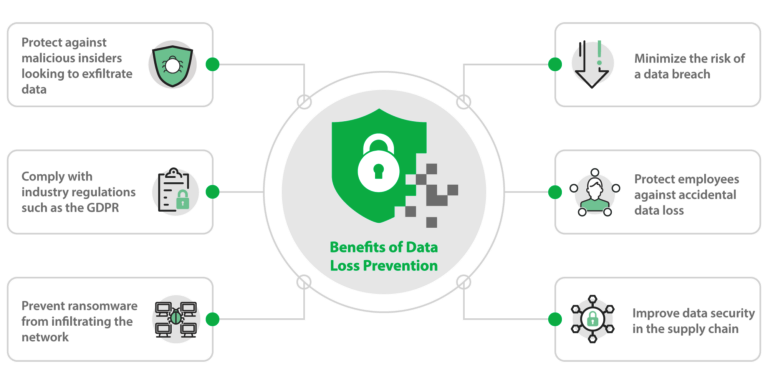
Data Loss Prevention (DLP) serves as a critical component of any compliance strategy, helping organizations protect sensitive data and ensure adherence to regulatory requirements. Whether governed by HIPAA, GDPR, ITAR, or other industry-specific regulations, organizations must implement DLP measures to mitigate the risks of data breaches, unauthorized access, and compliance violations. By identifying, classifying, and monitoring sensitive data, DLP solutions enable organizations to proactively safeguard their information assets and maintain compliance with regulatory mandates.
Key Components of DLP
- Identifying and Classifying Sensitive Data: DLP solutions leverage advanced algorithms and classification techniques to identify and classify sensitive data based on predefined criteria. This process involves scanning data repositories, analyzing content, and applying classification labels to data objects based on their sensitivity level.
- Monitoring Data Transfers and Activities: Effective DLP solutions monitor data transfers and activities within an organization’s network, identifying and mitigating potential security risks, such as data exfiltration attempts, unauthorized access, and policy violations. By establishing granular policies and rules, organizations can enforce data protection measures and prevent unauthorized data movements.
- Reporting on Data Breaches and Compliance Incidents: In the event of a data breach or compliance incident, DLP solutions play a crucial role in detecting, alerting, and reporting security events. By generating alerts, notifications, and comprehensive reports, DLP solutions enable organizations to respond swiftly to security incidents, investigate root causes, and remediate vulnerabilities.
- Providing Audit Trails and Logs for Compliance Audits: Compliance audits are a routine requirement for organizations subject to regulatory mandates. DLP solutions facilitate compliance audits by providing detailed audit trails, logs, and documentation that demonstrate adherence to regulatory requirements. These audit trails serve as evidence of compliance and help organizations streamline the audit process.
Types of DLP Solutions
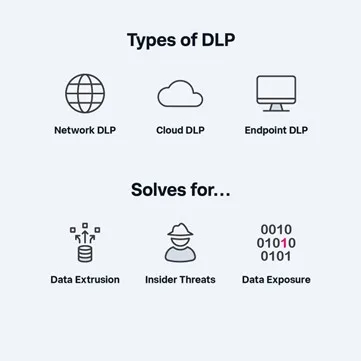
To address the diverse needs and challenges of data protection, organizations can leverage three broad types of DLP solutions:
- Network DLP: Focuses on protecting data in transit within an organization’s network, monitoring and controlling data flows to prevent unauthorized access and transmission. Network DLP solutions employ technologies such as secure web gateways (SWG) and cloud access security brokers (CASB) to inspect data in transit and enforce security policies.
- Endpoint DLP: Protects data on individual devices, such as laptops and desktops, by monitoring and controlling data access and transfer. Endpoint DLP solutions provide visibility into how individual users within an organization interact with data, enabling organizations to enforce security policies at the endpoint level.
- Cloud DLP: Designed to discover and protect critical data in the cloud across various storage systems and applications. Cloud DLP solutions focus on data discovery, classification, and protection within cloud environments, helping organizations identify and mitigate security risks associated with cloud-based data storage and sharing.
How DLP Solutions Operate
Each type of DLP solution operates through specific mechanisms to protect sensitive data:
- Sensitive Data Discovery: DLP solutions scan data repositories, including cloud storage, endpoints, and SaaS applications, to identify sensitive data and classify it based on predefined policies.
- Data Movement Monitoring: DLP solutions monitor data transfers and activities to detect unauthorized access, transmission, or sharing of sensitive information. This includes monitoring email communications, file transfers, web uploads, and other data movements within the organization’s network.
- Policy Enforcement and Incident Response: DLP solutions enforce security policies and rules to prevent unauthorized data movements and policy violations. In the event of a security incident, DLP solutions trigger alerts, notifications, and automated responses to mitigate risks and enforce compliance.
Challenges and Considerations
While DLP offers significant benefits in terms of data protection and compliance, organizations must navigate several challenges and considerations:
- Complexity and Configuration: DLP solutions can be complex to implement and configure, requiring significant technical expertise and resources. Organizations must invest time and effort in designing and customizing DLP policies to align with their specific security requirements and regulatory obligations.
- False Positives and Performance Impacts: DLP solutions may generate false positive alerts and impact system performance due to their intrusive nature. Organizations must fine-tune DLP policies to minimize false positives and optimize performance, balancing security requirements with operational efficiency.
- User Acceptance and Privacy Concerns: DLP solutions may be perceived as intrusive or restrictive by end-users, leading to resistance to adoption or use. Organizations must communicate effectively with employees, educate them about the importance of data security, and address privacy concerns to ensure user acceptance and compliance.
Best Practices for Implementing DLP
To maximize the effectiveness of DLP efforts, organizations should consider the following best practices:
- Start with a Comprehensive Risk Assessment: Conduct a thorough risk assessment to identify data security risks, regulatory requirements, and compliance obligations. Use the insights gained from the risk assessment to inform the design and implementation of DLP policies and controls.
- Establish Clear Policies and Procedures: Develop clear and concise policies and procedures that outline the organization’s approach to data protection, data classification, and incident response. Ensure that employees understand their roles and responsibilities regarding data security and compliance.
- Implement a Layered Approach to DLP: Adopt a layered approach to DLP by deploying a combination of network, endpoint, and cloud-based DLP solutions. This multi-layered approach enhances defense-in-depth and provides comprehensive protection across different data channels and endpoints.
- Regularly Monitor and Update DLP Controls: Continuously monitor and update DLP controls to adapt to evolving threats, regulatory changes, and organizational requirements. Conduct regular audits and assessments to ensure the effectiveness of DLP measures and address any gaps or vulnerabilities.
Leading Vendors and Core Competencies:
- Symantec (now Broadcom): Symantec offers a comprehensive DLP solution that helps organizations discover, monitor, and protect sensitive data across endpoints, networks, and cloud applications. Their DLP platform provides advanced capabilities for data classification, policy enforcement, incident response, and compliance reporting.
- Zscaler: Zscaler offers cloud-native security solutions, including Data Loss Prevention (DLP), to protect sensitive data across cloud applications, endpoints, and networks. Their platform provides real-time visibility, granular access controls, and encryption policies to maintain compliance and prevent data loss.
- Netskope: Netskope specializes in cloud security with a Cloud Access Security Broker (CASB) platform featuring robust DLP capabilities. Their solution enables organizations to discover, monitor, and protect sensitive data across cloud environments, ensuring security and compliance in the cloud era.
- McAfee (now Intel Security Group): McAfee provides a range of DLP solutions designed to safeguard sensitive data and ensure compliance with regulatory requirements. Their DLP offerings include solutions for network DLP, endpoint DLP, and cloud DLP, as well as integrated data protection suites for comprehensive data security.
- Forcepoint: Forcepoint offers a holistic approach to DLP, combining data discovery, classification, monitoring, and protection capabilities into a unified platform. Their DLP solutions enable organizations to identify and mitigate data security risks across on-premises and cloud environments while maintaining compliance with industry regulations.
- Digital Guardian: Digital Guardian specializes in endpoint DLP solutions that provide real-time visibility and control over sensitive data on laptops, desktops, and servers. Their DLP platform includes advanced features such as data discovery, user behavior analytics, and threat detection to prevent data breaches and insider threats.
- Skyhigh Networks (now McAfee Cloud Security): Skyhigh Networks, now part of McAfee Cloud Security, offers a cloud-native DLP solution designed to protect data stored in cloud applications and services. Their DLP platform provides visibility into cloud usage, detects sensitive data in real-time, and enforces security policies to prevent data loss and compliance violations.
- Cisco: Cisco provides a comprehensive DLP solution that integrates with their broader security portfolio, including network security, endpoint security, and cloud security offerings. Their DLP platform offers centralized policy management, content discovery, and incident response capabilities to help organizations protect sensitive data across the enterprise.
- Code42: Code42 specializes in endpoint DLP solutions that focus on data backup, recovery, and insider threat detection. Their DLP platform provides continuous monitoring of endpoint data activity, automatic file classification, and advanced detection algorithms to identify and respond to data security risks in real-time.
Conclusion: Safeguarding Sensitive Information with DLP
In an era characterized by data proliferation and cyber threats, Data Loss Prevention (DLP) emerges as a critical enabler of data protection and compliance. By implementing robust DLP measures, organizations can mitigate the risks of data breaches, unauthorized access, and compliance violations, ensuring the confidentiality, integrity, and availability of sensitive information.
With a comprehensive understanding of DLP principles, challenges, and best practices, organizations can harness the power of data protection and navigate the complexities of the digital landscape with confidence and assurance. Let DLP be your shield in safeguarding sensitive information and upholding the trust of your stakeholders in the digital age.
To learn more about our cybersecurity solutions, see: https://www.bytebt.com/cybersecurity/
About The Author
Sandesh Reddy
Sandesh is a Solutions Architect at ByteBridge with a strong background in security and networking. He specializes in Secure Access Service Edge (SASE) projects and holds certifications in CCNA, AWS, ZScaler, and Netskope. Sandesh is committed to driving innovation and delivering value-driven solutions to address the evolving needs of modern enterprises.







