In an era marked by AI-enabled cyber threats and evolving work models, traditional network security paradigms are proving inadequate. Enterprises are increasingly turning to Cloud-delivered Zero Trust Network Access (ZTNA) as a modern alternative to legacy VPNs. In this article, we explore the benefits and challenges of transitioning to ZTNA, highlight the role of AI in defending against sophisticated attacks, and provide insights into deploying a converged ZTNA/ SD-WAN architecture for seamless remote work capabilities.
What Is Zero Trust Network Access (ZTNA)?
So, what exactly is Zero Trust Network Access (ZTNA), and why is it gaining traction in the cybersecurity community? In essence, ZTNA is a security framework that assumes zero trust towards any entity trying to access resources on a network, whether it’s located within the corporate perimeter or in the cloud. Unlike traditional network security models that rely on perimeter-based defenses, ZTNA adopts a more granular approach by authenticating and authorizing users and devices on a per-session basis, regardless of their location or network environment.
One of the key principles of ZTNA is the concept of least privilege access, which restricts user access to only the resources and applications necessary to perform their job functions. By implementing strict access controls and micro-segmentation, organizations can minimize the attack surface and reduce the risk of unauthorized access and lateral movement within their networks.
How Does ZTNA Work?
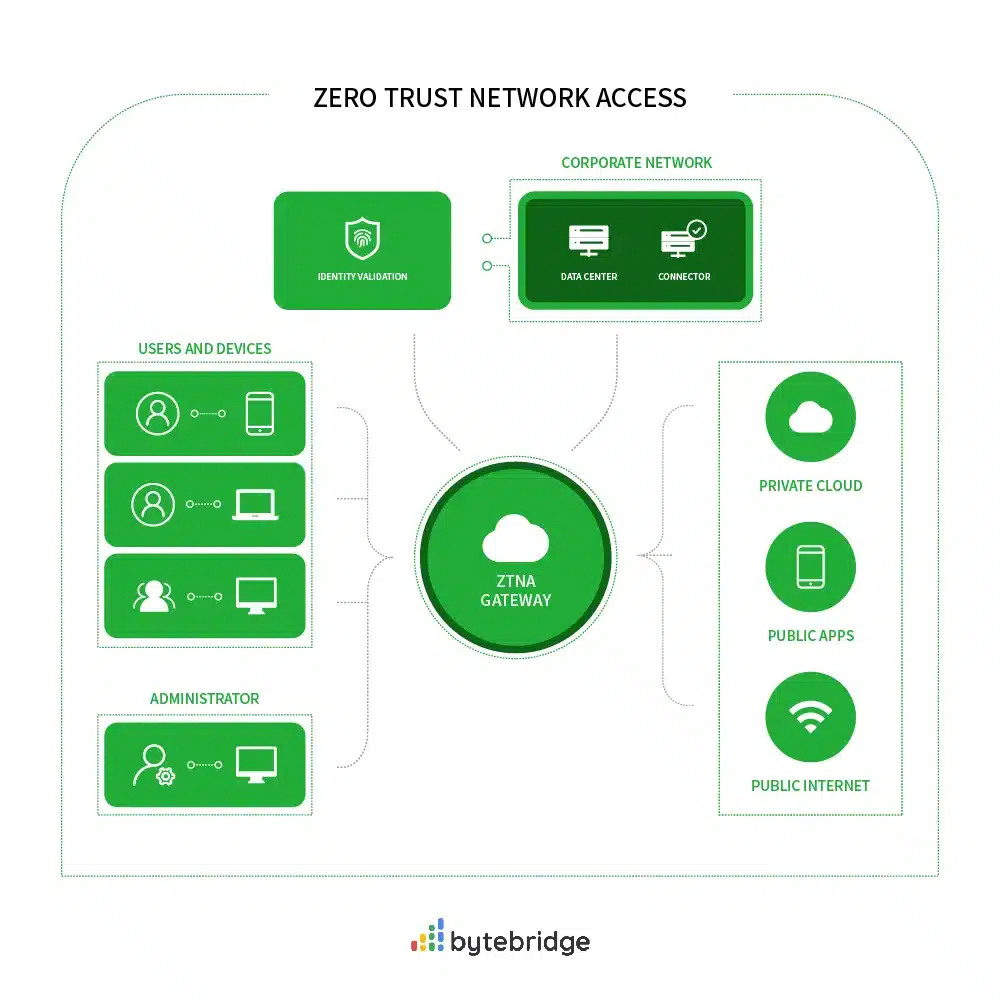
ZTNA operates by establishing secure connections between users or devices and the applications or resources they intend to access, without granting blanket access to the entire network. This is achieved through rigorous identity verification, device posture assessment, and encryption mechanisms. Users must undergo multi-factor authentication (MFA) or other robust authentication methods before gaining access to the requested resources. Additionally, ZTNA solutions often incorporate micro-segmentation techniques to enforce access controls at the application level, further bolstering security.
Benefits of ZTNA
The adoption of ZTNA offers numerous benefits for organizations, including:
- Enhanced Security: ZTNA minimizes the risk of unauthorized access and data breaches by enforcing strict access controls and authentication mechanisms.
- Improved User Experience: With ZTNA, users can seamlessly access applications and resources from any location or device, without compromising security.
- Flexibility and Scalability: ZTNA solutions are highly adaptable and scalable, making them suitable for organizations of varying sizes and industries.
- Reduced Operational Complexity: ZTNA simplifies network management and reduces the need for complex VPN configurations, leading to lower operational costs.
What Is the Difference Between VPN and ZTNA?
While VPNs provide secure remote access to corporate networks, they typically grant access based on network location, which can pose security risks, especially in the context of remote work and cloud adoption. In contrast, ZTNA takes a more context-aware approach, verifying the identity and security posture of users and devices before granting access to specific applications and resources. This ensures that only authorized users can access sensitive data, irrespective of their location or network environment.
How Do You Implement ZTNA?
Implementing ZTNA involves several key steps:
- Assessment: Conduct a comprehensive assessment of your organization’s network infrastructure, security policies, and business requirements to identify potential vulnerabilities and risks.
- Planning: Develop a detailed plan for implementing ZTNA, including defining access policies, selecting appropriate authentication methods, and evaluating ZTNA solutions.
- Deployment: Deploy ZTNA solutions, leveraging ByteBridge’s expertise and partnerships with industry leaders such as Netskope, Palo Alto Networks, and Zscaler, to enforce access controls and secure connections between users and resources.
- Optimization: Continuously monitor and optimize your ZTNA deployment to ensure compliance with security policies and address any emerging threats or vulnerabilities. Additionally, consider deploying a converged ZTNA/SD-WAN architecture to enhance remote work capabilities and ensure seamless connectivity.
In conclusion, Zero Trust Network Access (ZTNA) represents a revolutionary approach to network security, offering organizations the means to proactively protect their critical assets in an increasingly digital world. With ByteBridge as your trusted partner, you can navigate the complexities of ZTNA implementation and harness its benefits to fortify your security posture and enable seamless remote work capabilities.






